Let’s solve the Chromatica machine from hackmyvm.
It is the easy machine with SQLi which give us few password hashes and usernames, then we need to SSH (which is little bit tricky) and then exploit the cron job to get shell as another user. Then there is a privilege escalation using sudo by nmap command.
Let’s begin with nmap to enumerate the open ports and services running on those ports. Nmap shows only three ports open.

Use wfuzz or dirb to bruteforce webpages and directories on web app.

When I visit the robots.txt, I got below entry.

I tried to visit dev-portal, but got Forbidden.

I tried to fuzz using wfuzz, but did not get any additional directory or web page. Then I change tried changing the User-Agent header to dev and tried to access the dev-portal.
I added the rule in burp suite to replace User-Agent header with that of “User-Agent: dev” and then visit the /dev/portal and it shows me below web page.

This page allow us to search cities.

Let’s use SQLmap to find sql injection. For that save the request in a file and use that with SQLmap. Sqlmap says the URL is vulnerable.

SQLmap discovered couple of databases.

Let’s enumerate Chromatica database and try to find the tables in it.

We are interested in users table, lets enumerate the columns of users table.

Let’s find username and password.

I use crackstation to crack the remaining hashes.

Stored username and hashes in separate files to bruteforce SSH login. Used hydra and it found the correct combination.
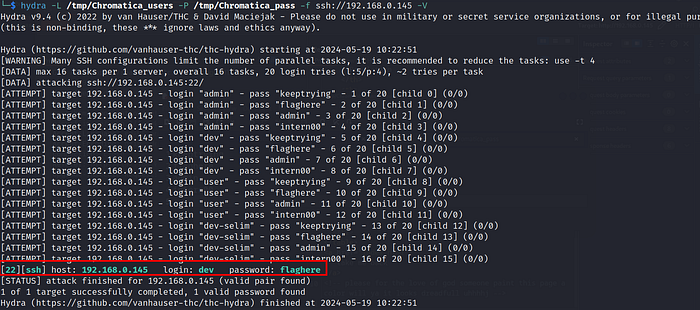
As soon as I tried to login in ssh, I did not get the access to the box.

I again enumerate the /dev-portal directory and found login.php
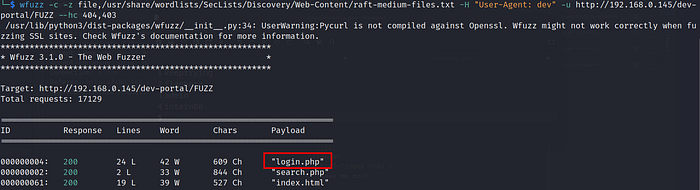

The login.php was a rabbit hole. I again moved towards SSH, reduced the size of my terminal to minimum I can do and the use !/bin/bash after my creds when it shows more option.


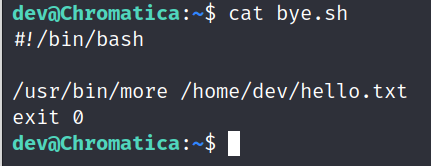
While enumerating the box further, I noticed a cron running every minute with user analyst.

Let’s see the permission and contents of a shell script /opt/scripts/end_of_day.sh

That is very dangerous permission as whole world can read and write into it. We can write a reverse shell code into this which can call back us at a listener.

I use command to check sudo permissions for user analyst and it shows analyst can run nmap without password.

using nmap, able to escalate the privilege to the root.

So this is how we are able to get the root on the box Chromatica from hackmyVM.
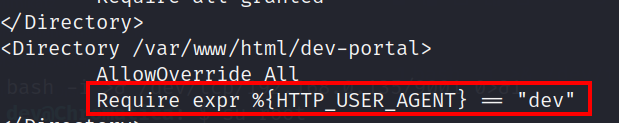
I searched for why we are unable to get the dev-portal with normal User-Agent, the apache2.conf file has below line mentioned which blocked us from accessing dev-portal with normal user agent.